Security Aware Developer

This unique security training was developed as a result of hundreds of meetings with developers and entire project teams. We put emphasis not only on the unique formula, but also on exceptional practicality. Our strong belief is that prevention is better than cure. That is why we are taking a few steps back to ensure the proper level of security for your IT solutions.
Training goals:
The scenarios presented during the workshops are based on our experience in penetration testing and infrastructure audits. We provide participants with a new perspective on security.
The main goals of the training are:
- Raising developers, architects, and testers’ awareness about application security issues, their causes, and possible outcomes,
- Showing lots of real-life examples,
- Discussing possible preventive measures and their pros and cons related to a vulnerability chain described in a given scenario.
The need for security is constantly increasing:
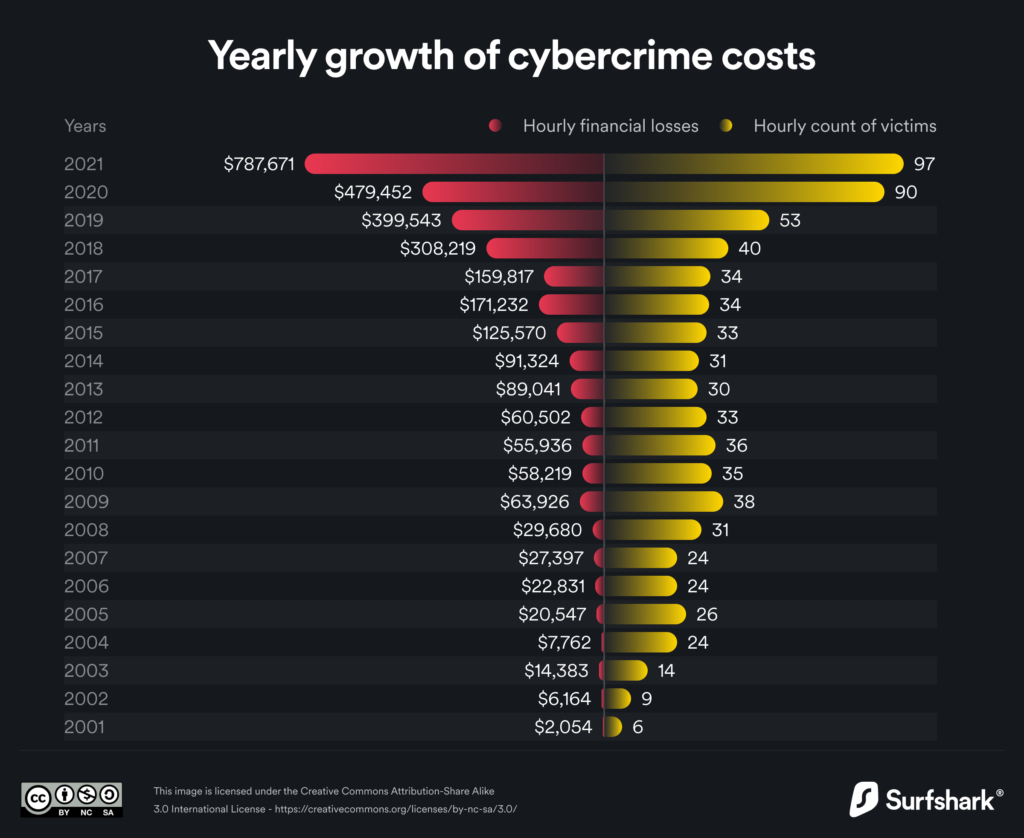
Year after year, as software complexity is growing, the number of security-related issues is also getting bigger. This affects a demand for secure components and for the entire infrastructure of newly developed and maintained solutions. Only at the very end of the software development lifecycle, penetration tests may help to find vulnerabilities, though, they may also lead to lengthening or even delays in new releases. Moreover, a pentest done once a year, when application changes daily, may not be enough.
Incorporating security early into SDLC not only shortens the whole process but also makes it more cost-effective.
Based on the feedback, we see that discussions and ideas which sprang out during training increase awareness among participants. This inspires them to implement new app-security ideas that sprouted during the training in their daily work.
About the trainers:

Mateusz Olejarka
Principal Security Consultant | Head of Web Security
His key responsibilities are web and mobile application penetration testing and source code review. Moreover, he works as a consultant helping software development teams cope with application security topics. He performed more than 60 application security trainings dedicated to software developers. Previously working as a software developer, building software for the financial sector. He was a speaker both at international and Polish conferences and meetings dedicated to software development and IT security. Casual bug bounty hunter, listed in Hall of Fame companies like Adobe, Algolia, GM, Jet, Netflix, Tesla, Twitter, Uber, and Yahoo.
Certificates: OSWE (Offensive Security Web Expert), CEH (Certified Ethical Hacker)
Representation at conferences: 4Developers, Black Hat Asia, Code Europe, CONFidence, Hacktivity, NGSec, Security Case Study, Secure, SEMAFOR, Testing Cup, TestWarez, TestWell, OWASP and KraQA meetings.

Jakub Korepta
Principal Security Consultant | Head of Infrastructure
Started his professional career in one of the biggest telecommunications companies, where he worked as a software engineer developing a generic test automation framework and conducting security-related trainings. In SecuRing, his key responsibilities are web and mobile application penetration testing, network infrastructure security assessment, and source code review. Member of Dragon Sector CTF team.
Certificates: OSCP
Representation at conferences: CyberTech Tel Aviv 2017

Dawid Pastuszak
Security Consultant
He started his adventure with cybersecurity at a very young age. He has already performed dozens of penetration tests in his commercial experience. In addition to finding vulnerabilities in mobile and web applications, he specializes in Apple mobile devices and is also interested in binary exploits. Dawid also researches different topics, such as iOS application builds.
Certificates: eCXD (eLearnSecurity Certified Exploit Developer), eLearn Web Penetration Tester Extreme (eWPTXv2)
The training agenda:
Each solution is different. Thanks to the fact that our training is modular, we can adjust it to specific environments. We have prepared many different scenarios to include in your workshops. They may include:
- XXE – Access control error, Incorrect processing of XML files, Execution of any command on the server, Stealing files from the server
- XSS – Validation error, Stored XSS in Angular templates, Permanent application crash
- PHISHING – How to take control of the code? Phishing, Obtaining a login and password for one of the developer websites, SSO abuse, Obtaining access to the source code
- ESCALATION – Redundant application module, Default settings, Saving sensitive data to logs, Obtaining application administrator privileges
- SQL INJECTION – Non-obvious example of SQL Injection and home cryptography
- BANK – Case study of one of the banks: Defect in a component, Taking control of the frontend, JavaScript modification, Bypassing additional authorization, Theft of funds from accounts
There are also modules dedicated to the specificity of the developer’s workplace.
Join the list of the companies that care.
If you want to see the full training or book it for your organization – use our contact form by clicking “write to us”.
We have conducted over 70 workshops and trained over 600 members of project teams. We are proud to observe that more and more companies prioritize Security in software development lifecycles. We encourage you to join this movement!





